 From late March 2020, when the global pandemic Covid-19 paralysed many economies, the appeal of cryptocurrencies has grown. Several statistics show increased interest from downloaded wallet apps to peer-to-peer traded volumes. In many ways, this interest in bitcoin and altcoins is evidence that the policies of central banks are failing. Many professional investors, as well […]
From late March 2020, when the global pandemic Covid-19 paralysed many economies, the appeal of cryptocurrencies has grown. Several statistics show increased interest from downloaded wallet apps to peer-to-peer traded volumes. In many ways, this interest in bitcoin and altcoins is evidence that the policies of central banks are failing. Many professional investors, as well […]
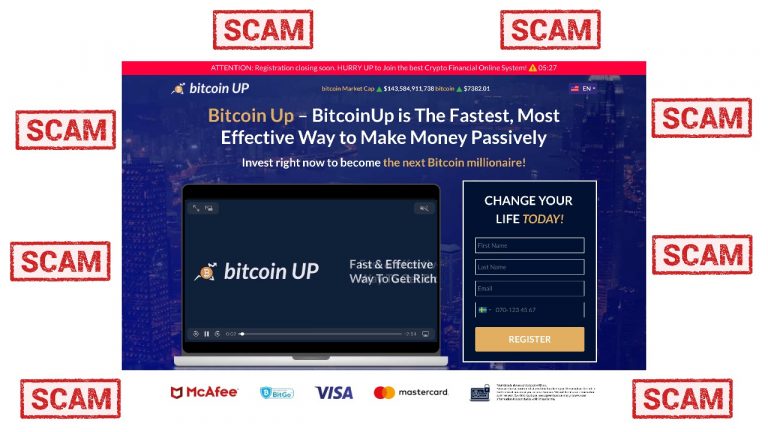
The post The Tell Tale Signs of a Scam Crypto Website: Bitcoin-Up.Live appeared first on Bitcoin News.
Powered by WPeMatico



 Hash power broker Nicehash denies that it enables bad actors to use its hash renting platform to launch 51% attacks on blockchain networks. The broker insists that it does not have any way of monitoring or determining which blockchain is benefitting from a particular algorithm hash data. Only buyers of hashrate know this, as well […]
Hash power broker Nicehash denies that it enables bad actors to use its hash renting platform to launch 51% attacks on blockchain networks. The broker insists that it does not have any way of monitoring or determining which blockchain is benefitting from a particular algorithm hash data. Only buyers of hashrate know this, as well […]
 Reports in the past few weeks detail that bad actors are targeting two privacy coin projects, Monero and Zcash, adding to concerns about the growing rate of security incidents involving blockchain networks. Such incidents, as well the repeated 51% attacks on the Ethereum Classic network or the Electrum wallet breach, suggest criminals are becoming more […]
Reports in the past few weeks detail that bad actors are targeting two privacy coin projects, Monero and Zcash, adding to concerns about the growing rate of security incidents involving blockchain networks. Such incidents, as well the repeated 51% attacks on the Ethereum Classic network or the Electrum wallet breach, suggest criminals are becoming more […]
 A new trojan called Krypto Cibule uses infested computers’ power to mine cryptocurrency, steal crypto wallet files, and redirect incoming digital assets to a hacker address. The malware rides on the Tor network and the Bittorrent protocol to perform attacks, according to an extensive report by cybersecurity company, ESET. “Krypto Cibule is spread through malicious […]
A new trojan called Krypto Cibule uses infested computers’ power to mine cryptocurrency, steal crypto wallet files, and redirect incoming digital assets to a hacker address. The malware rides on the Tor network and the Bittorrent protocol to perform attacks, according to an extensive report by cybersecurity company, ESET. “Krypto Cibule is spread through malicious […]